How to configure the switch to prevent IP scanning
 Zyxel Employee
Zyxel Employee



In this example, we will use Anti-ARP Scan to prevent attackers from identifying all network devices in the local area network. ARP Scanning is a method by which attackers send multiple ARP request packets in a very short period of time to flood across the entire broadcast domain.
Note:
All network IP addresses and subnet masks are used as examples in this article. The Access Point in this section uses the default Radio and SSID Profile. For this section, we will refer to “Zenmap” as the IP Scanning tool. All UI displayed in this article are taken from the XGS4600 series switch.
1. Configuration in the Switch
1-1. Access the Switch’s Web GUI.
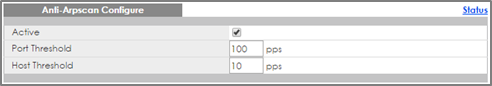
1-2. Go to Advance Application > Anti-Arpscan > Configure. Check the Active box and configure the uplink port (port 24) as “Trusted” state. Click Apply.
1-3. (Optional) Go to Advance Application > Errdisable > Errdisable Recovery. Check the Active box and anti-arpscan box. Click Apply.
2. Test the Result
2-1. Download and install an IP Scanning software into Host-A and Host-C.
2-2. Connect Host-A and Host-B via the Wireless Access Point.
2-3. Host-A should initiate a scan for IP address 192.168.1.1 to 192.168.1.20.
2-4. Host-A should no longer be able to reach the USG.
2-5. Access the Switch’s Web GUI. Go to Advance Application > Anti-Arpscan > Host Status. An entry for Host-A should appear with an “Err-Disable” state.
Note:
If Errdisable Recovery has been configured, the Host-A entry should recover after the Errdisable Recovery Interval. Host-A will be able to reach the USG, afterwards.
2-6. Host-B should still be able to reach the USG.
2-7. Connect Host-C to the Switch.
2-8. Host-C should perform a quick scan for IP address 192.168.1.1 to 192.168.1.100.
2-9. Host-C should no longer be able to reach the USG.
2-10. Access the Switch’s Web GUI. Go to Advance Application > Anti-Arpscan. Port 2 should now be in an Err-disabled state.
Note:
If Errdisable Recovery has been configured, Port 2 state should change to forwarding after the Errdisable Recovery Interval. Host-C will be able to reach the USG, afterwards.
3. What Could Go Wrong
3-1. If access to servers or the local gateway is no longer possible after enabling Anti-Arpscan, make sure that only ports directly connected to hosts or Wireless Access Points are “untrusted”. Ports to servers and the local gateway should be “trusted”.
3-2. If all hosts connected through a Wireless Access Point can no longer reach the local gateway, check whether the port to the Wireless Access Point has changed to the err-disable state in Advance Application > Anti-Arpscan. If so, consider increasing the Port Threshold in Advance Application > Anti-Arpscan > Configure.
Categories
- All Categories
- 383 Beta Program
- 2.1K Nebula
- 116 Nebula Ideas
- 80 Nebula Status and Incidents
- 5.1K Security
- 75 USG FLEX H Series
- 247 Security Ideas
- 1.3K Switch
- 69 Switch Ideas
- 907 WirelessLAN
- 34 WLAN Ideas
- 5.9K Consumer Product
- 210 Service & License
- 335 News and Release
- 71 Security Advisories
- 21 Education Center
- 5 [Campaign] Zyxel Network Detective
- 1.9K FAQ
- 886 Nebula FAQ
- 415 Security FAQ
- 228 Switch FAQ
- 200 WirelessLAN FAQ
- 46 Consumer Product FAQ
- 137 Service & License FAQ
- 34 Documents
- 34 Nebula Monthly Express
- 73 About Community
- 62 Security Highlight